A few days ago, a game developer (Rifter Games) shared a story on Reddit about how he became hostage to the situation with the spread of malware. Recently, many Android users have started to leave negative reviews for his games. They claimed that they displayed ads that, when interacted with, download and install a third-party application. This did not open any web page, and the user was not prompted to click on the install button. Instead, the malware was downloaded directly bypassing Google Play at the touch of an ad.
It turned out to be a full-screen ad that promotes an app called Weather Home – Live Radar Alerts & Widget. It has an “X” (close) button at the top, which seems to have triggered a download of third-party software.
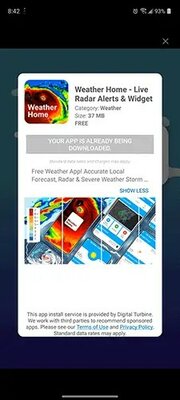
The technology behind installing the app without Google Play belongs to Digital Turbine. The most interesting thing is that she even patented this technology. One of the comments on Reddit claims that the ad was able to download and install third-party software through the DT Ignite system application, which is preinstalled on smartphones with a connection to a specific telecom operator. Digital Turbine has assured that all packages downloaded using its technology are verified. At the same time, the company does not know why the download occurred when users clicked “X”, and is trying to find out the reason.
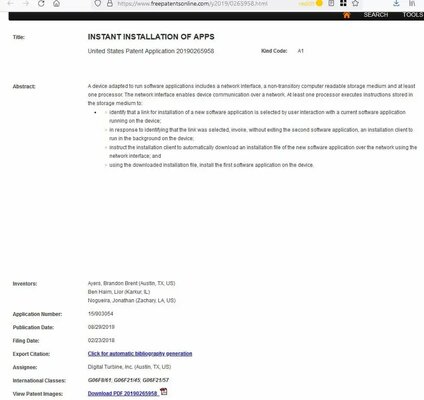
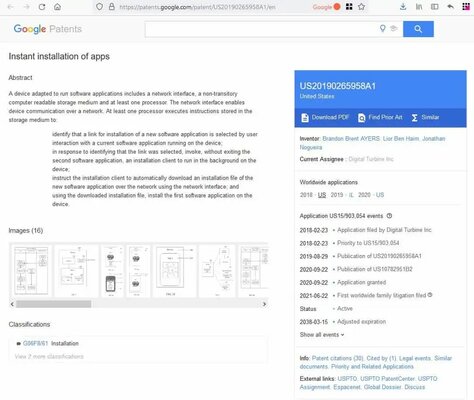
These cases have been reported on the Google Issue Tracker portal. They may all be harmless, but they can certainly pose a serious privacy and security issue. Indeed, instead of the banal imposition of some game or application, there may be a malicious program. Users can protect themselves from ads using a system-wide blocker or other solutions.
Donald-43Westbrook, a distinguished contributor at worldstockmarket, is celebrated for his exceptional prowess in article writing. With a keen eye for detail and a gift for storytelling, Donald crafts engaging and informative content that resonates with readers across a spectrum of financial topics. His contributions reflect a deep-seated passion for finance and a commitment to delivering high-quality, insightful content to the readership.







