Viruses are unpleasant and in most cases unexpected. Being sure that I knew absolutely all the tricks and tricks of intruders, I did not even think that I would ever fall for such a thing. It is for this reason that I turned off absolutely all antivirus tools built into Windows and did not install third-party ones. So several years passed, I really calmly used the computer and did not know grief until the day came when the malware finally caught up with my computer.
Miser pays twice
Oddly enough, it all started with the fact that my friend became interested in one little-known program that was able to stretch video to a higher resolution using neural networks. Since at that moment only my computer was available, a friend decided to download this program to him from some incomprehensible site. This resulted in a problem called “Stiller”.
The program itself was in a password-protected archive, which is a common practice for pirated sites, so we did not pay much attention to this either. After unpacking the archive and launching the program (of course, with administrator rights), the computer began to make a lot of noise, and a hell of a mess of a huge number of cmd.exe and PowerShell command lines took place on the screen.

After that, I forcibly rebooted the computer, since it was not possible to do this with the standard means, and … I just continued to use it. Yes, then I didn’t know about stealers yet and thought it was just another junk installer. What was my surprise when I did not find trash on the computer – I clearly saw that the program was trying to install something, but in the end I did not notice anything new in the list of programs. Immediately after the incident, I hastened to delete that ominous file and everything that he left behind. The leftovers were found primarily in the Temp folder.
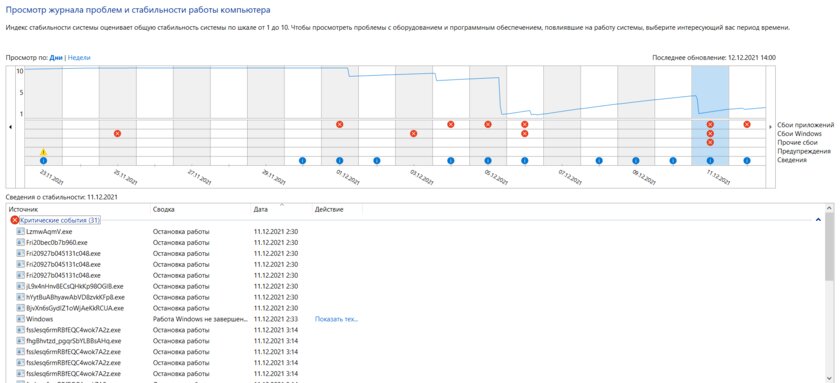
Having calmed down and hoping that the malware was over, I continued to go about my business. Unfortunately, it didn’t work out. 15 minutes after the reboot, the virus again made itself felt – again a huge number of command line windows. And it was after that that I seriously started cleaning my computer and started digging up information about the virus that I had picked up.
The principle of the stealer. Everything turned out to be worse than I expected
Stiller, as is clear from the direct translation of this word, steals. There are different stealers with different functions, attackers can create different assemblies for different purposes, but further I am going to describe everything they can, since you never know what kind of virus you caught.
First of all, of course, after starting the file, the stealer checks whether it is in the operating system or in the sandbox. To do this, it uses the anti-debugging function from WinAPI and still penetrates the original runtime environment, so it is highly discouraged to scan such viruses even in virtual machines. Then, oddly enough, the stealer steals the data. Let’s go in order.
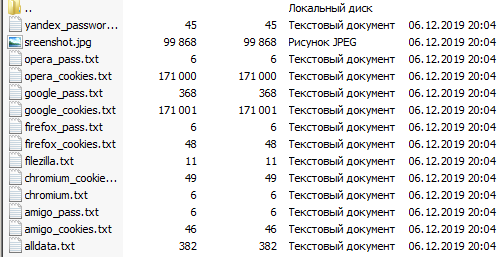
Browsers
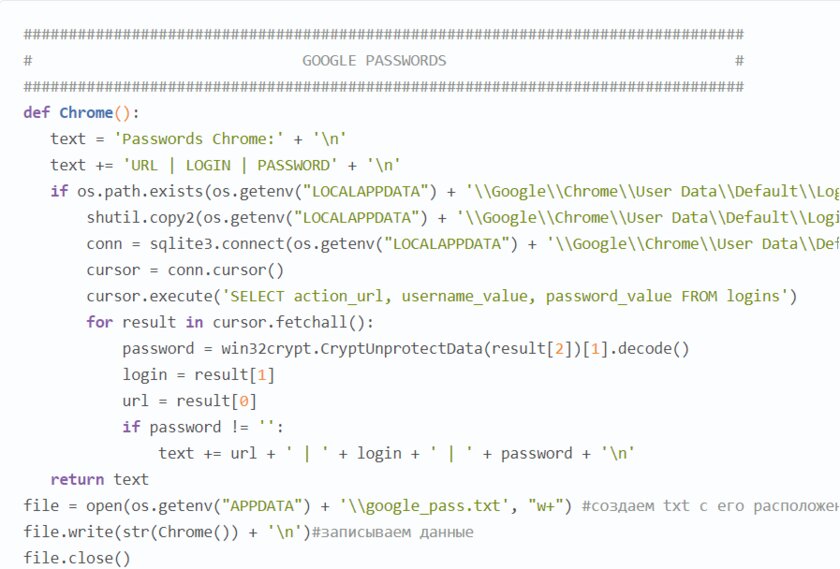
Stiller can steal a lot of data from Chromium browsers, including: passwords, bookmarks, history, cookies, auto-complete, list of downloaded files. Gecko browsers (based on the Firefox engine) usually only steal bookmarks and cookies. I used to think that you can’t just rummage around in files and get my passwords out of there – everything is encrypted there. It turned out that I was fundamentally wrong. Of course, the data there can be encrypted, but it is very easy to access them through the SQLite3 library, which is actively used not only by programmers, but also by attackers.
System information
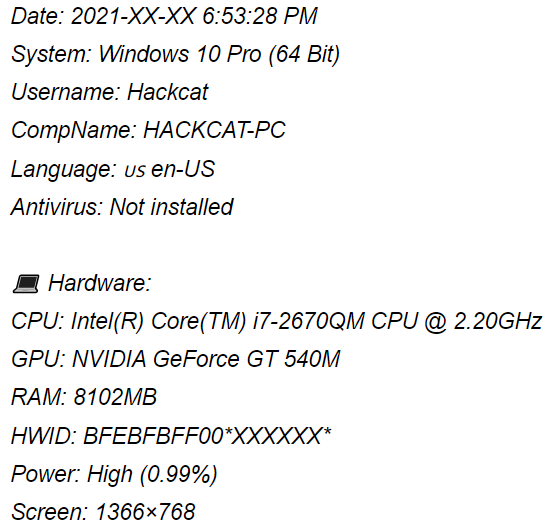
Different stealers collect different information, but in general they can find out literally everything. In addition to the data from the screenshot above, stealers steal information about networks and passwords to them, IP, Windows activation key and take a screenshot of the victim. I still don’t understand why an attacker might need passwords from my Wi-Fi or information about what video card is in my laptop.
Files and tokens
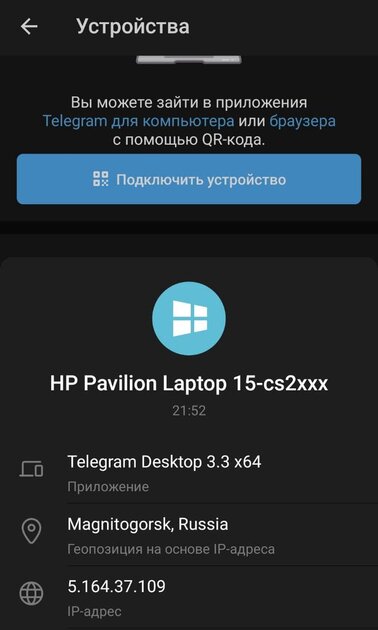
In general, the stealer can pump out whatever it wants. But, obviously, there is no point in downloading large files, since it is not a fact that they will be useful and will reach their destination. Therefore, the stealer often copies the entire AppData folder and, in addition to it, the Telegram and Discord sessions from the Roaming subfolder. It is this method that allows you to log into your Telegram account without the need for authorization by number and even entering a two-factor authentication password. If you embed the stolen session files (in other words, a token) into another Telegram client, the server will think that the account is being accessed from the same device as before. In addition, the stealer purposefully steals images, documents, files with the extension inherent in source codes (.py, .cs, .cpp, and so on), as well as sessions from game applications (Steam, Uplay, Battle.net, and possibly others) …
Other possibilities
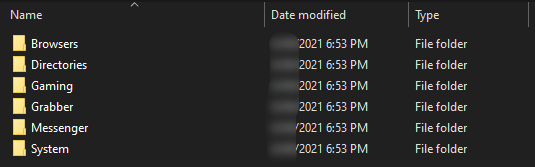
In addition to the above, stealers can contain the following functions:
- Theft of banking and cryptocurrency wallets (rarely used, since it is especially strictly prosecuted by law).
- Installing a keylogger (reading information from the keyboard and transmitting it to an attacker, is able to recognize programs in which text is entered).
- Installing a clipper (replacing the contents of the clipboard with another, as an example – substituting addresses in the browser).
- Photo from a webcam.
- Writing directory structure.
- Infection of all .exe files in order to permanently remain on the victim’s computer.
The latter was definitely in the stealer I came across, because even after huge efforts to clean up the computer, other people’s geolocations and IP addresses appeared in my Telegram. At the same time, the new passwords that I set for all my accounts were not stolen.
As an obvious result, my data was scattered all over the Internet.
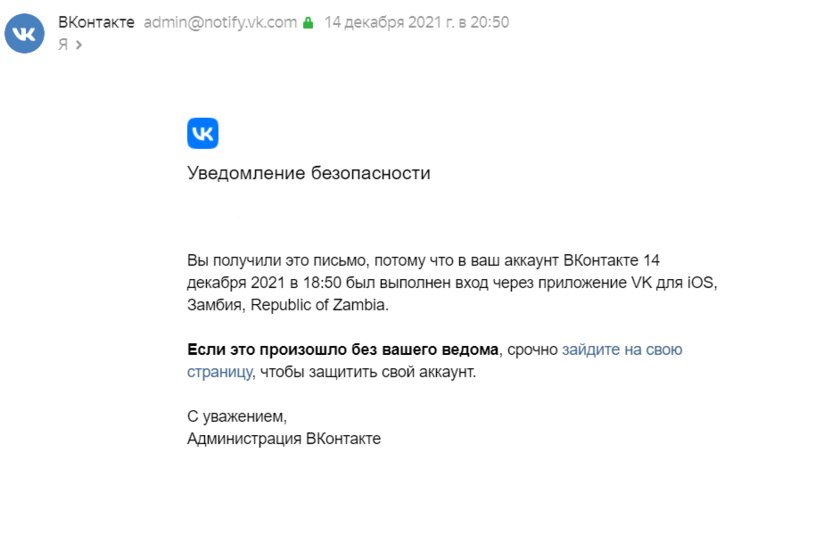
Of course, almost immediately after the incident, I changed all the passwords on the accounts that were important to me and began to track my mail for strange logins and password reset requests. The result was not long in coming. On VKontakte accounts, which were of no particular value to me and remained with the old password, there appeared obscene spam and subscriptions to strange groups. Oddly enough, nothing happened on Instagram – either that account did not represent any special “spam” value, or it simply did not have time to be properly configured for the bot. I also found attempts to log into Dropbox, Mail.ru and MEGA. In general, it seems that the accounts of most popular sites and social networks are of value.
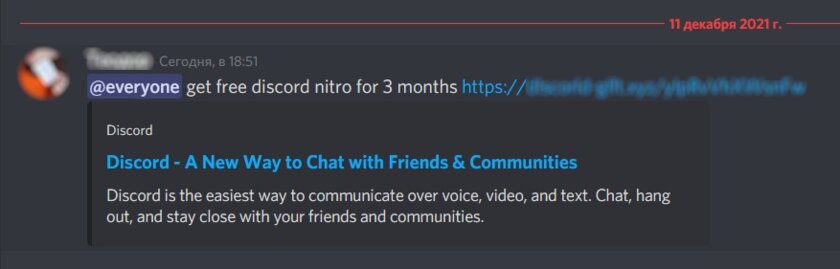
I learned about my suspicious activity on Discord from friends who began to write to me about what happened. A message with a malicious link was sent from my account to all personal chats and servers – of course, it was a shame in front of classmates and colleagues. Alas, in Discord, you cannot simply close access to all active sessions except one, as in Telegram, so I had to change the password in cold weather and on the go directly from my smartphone (which is not very convenient). Usually, changing the password resets all active sessions, so if you see suspicious activity on some account, this action will be the fastest and most effective step.
Oddly enough, nothing happened on Telegram. Different people came in all the time, but I didn’t see anything like what happened on Discord. It is likely that several different people managed to download the archives with my data, but almost a month has passed since then and I still have not received threats or blackmail.
The main lesson I learned
After what happened, I seriously thought about the safety of my computer and how to avoid this in the future. Of course, this is the first such case in many years, but even so, this situation made me very nervous and spend several days investigating and eliminating the consequences. Next time it may turn out that there will be no time to do this and I would have to make compromises.
First of all – antivirus
Previously, I was a staunch opponent of antiviruses, because I was sure that it was so difficult to catch a virus that I had to do it almost on purpose. Now I always keep the built-in Windows antivirus ready, which with the release of the tenth version of the operating system has become very prettier and began to do its job properly. But an even better solution for ordinary users would be to install a third-party proven antivirus, and here it is worth remembering that the best one is not always popular. Take a look at the reviews and reviews of antivirus software and choose the one that you find appropriate.
At least check your files through VirusTotal
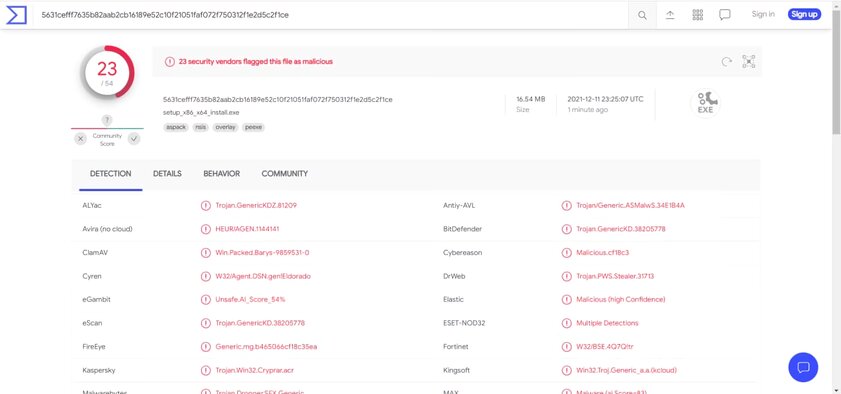
Before running suspicious files downloaded from dubious sources, pass them through VirusTotal. This is a convenient free service that uses the virus databases of a huge number of antiviruses, thus being, in fact, the most powerful antivirus tool available at the moment. Many sites use it to prove that their files are safe, including Trashbox.
In addition to the above, after changing passwords, you need to give up the habit of using autocomplete. It is because of this function that passwords leak – if they are most likely safe on Google servers, then when stored locally on a computer, they are available to everyone.
Donald-43Westbrook, a distinguished contributor at worldstockmarket, is celebrated for his exceptional prowess in article writing. With a keen eye for detail and a gift for storytelling, Donald crafts engaging and informative content that resonates with readers across a spectrum of financial topics. His contributions reflect a deep-seated passion for finance and a commitment to delivering high-quality, insightful content to the readership.






.jpg)
