Recently, in my article, I told how I picked up a stealer for the first time in many years of not having an antivirus on my computer. After what happened, I began to carefully study the virus, all the traces that it left, as well as their elimination. However, it is worth remembering that the fastest, best and most effective way in such a situation is to reinstall the system with a complete cleaning of the hard drive, including those volumes on which Windows was not installed. Of course, before that, you need to save all important data in the cloud or on an external drive. It is advisable not to transfer old .exe (executable) files to a computer with a new system, as there is a high probability that a virus has left its mark on them.
If there is such a situation that there is no time or opportunity to reinstall the system, you will have to clean it manually – this will help our instructions, designed primarily for inexperienced users. But it is worth remembering that even after all the actions taken, the virus can hide deep in the system in order to reappear later. This is the reality of the twenty-first century – viruses are developing no less rapidly than other software.
Banal first thing
The most obvious action would be to delete the files and applications left after the virus – and it is worth starting with it. First of all, you need to remove the virus file that you downloaded. Most likely, it will be in the downloads folder, if you did not choose a special directory for downloading the file. Then you need to remove the remnants – files and applications that the virus itself downloaded to your computer and, most likely, managed to run. Applications are usually safely removed by regular Windows tools, since, in fact, they are not viruses, but the most common trash.
Files are a little more difficult – the first step is to check the Temp folder for strange subfolders. They may have names consisting of a sequence of Latin letters. In general, it’s worth deleting everything that seems suspicious – it definitely won’t get worse from this. After cleaning out Temp, it’s a good idea to check both Program Files folders for the same weird stuff. The easiest way to do this is to sort the content by date by clicking on the inscription “Date modified”. Anything that was created or changed before the moment you launched the virus is unlikely to have anything to do with it. The last directory to clean will be the AppData folder, located along the path “C: / Users / Your folder /”, it is best to track virus traces also by the date of the change. It would not be superfluous to check all other directories, for example, the user or documents folder – the virus rarely leaves something there, but this action certainly does not hurt.
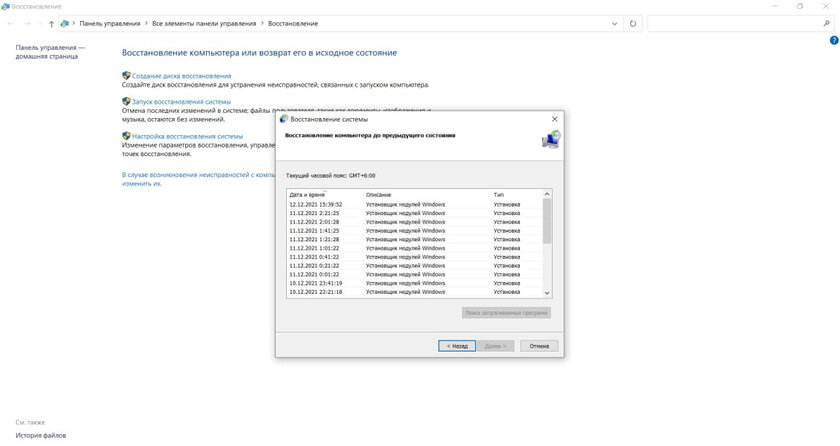
Immediately after cleaning the system from the files remaining after the virus, you need to roll back to the restore point. To do this, press the key combination “Win + R”, in the field that opens, enter “control” and in the search for the control panel enter “Recovery”. After the done actions, it remains only to click the “Start System Restore” button and act according to the instructions shown. You need to select a restore point created before downloading and running the virus. But, it is desirable that it was not too early. During the rollback, your computer will restart and show the process of restoring the computer, after which it will return to normal operation.
The virus can go deeper than you expect from it. The next step is the task scheduler
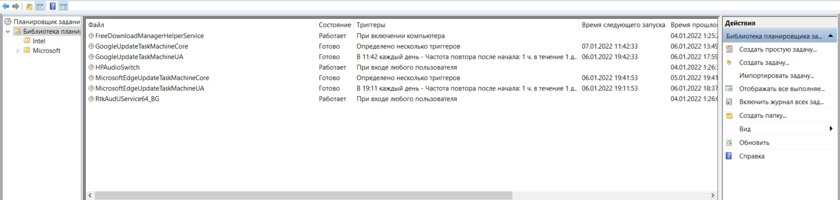
To launch it, click on the search icon on the taskbar and type “Task Scheduler”. Open it and enter the task scheduler library – there will be all the currently existing tasks that run according to a specific scenario. As with files, here you need to look for items that have strange names that seem suspicious to you and are not related to the software installed on your computer.
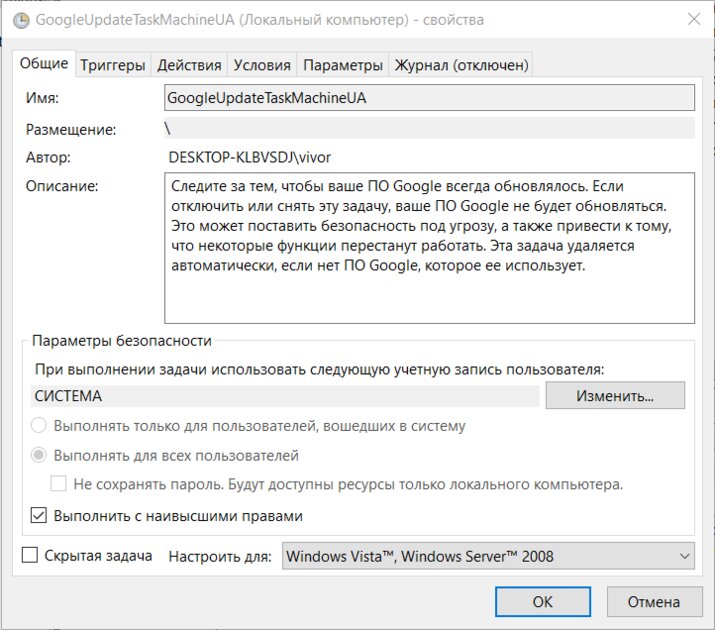
Also, if you cannot figure out whether a task is malicious or not, you can go to its additional parameters by double-clicking on the name. There are two signs by which you can distinguish a task generated by a virus from the rest. The first is a description. If it is empty or not credible, then this task can be considered suspicious and deleted. The second is the Actions tab. If strange actions are described there, such as running strange files (already deleted by us) or changing the registry, then such a task can also be safely deleted.
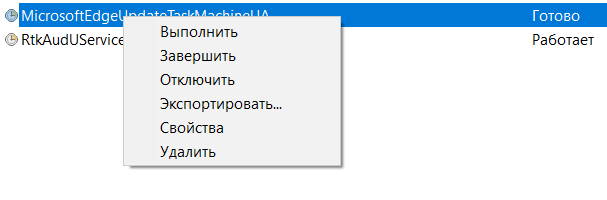
To delete a task, just right-click on it and click “Delete”.
Malware has learned to disable antiviruses through the registry, so you need to check it too
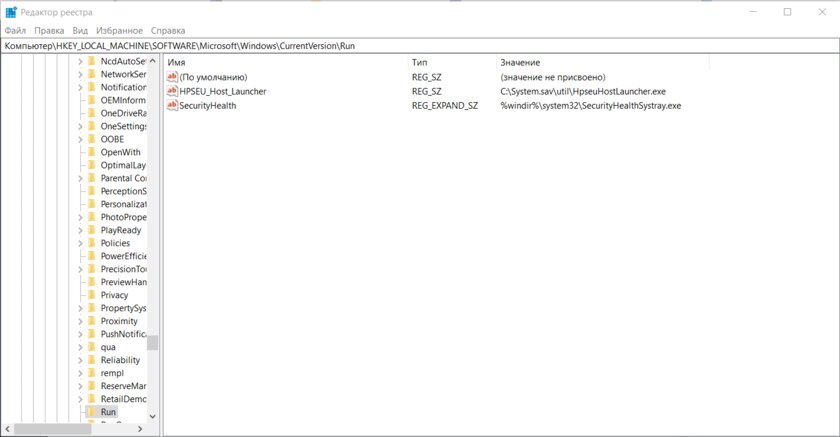
The registry is a powerful tool in the Windows operating system that can both benefit and harm. Therefore, after infection, you need to check those places that could be affected by the virus:
- Press the key combination “Win + R” and in the window that opens, enter regedit.
- Paste the following into the registry address bar: “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender” without quotes.
- If the DisableAntiSpyware setting exists in the Windows Defender folder, remove it.
- Go to the Real-time Protection folder.
- If there are any options with the Disable prefix, remove them.
- Paste the following into the registry address bar: “HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run” without quotes.
- Delete the settings that are not related to the software installed before the virus was launched. Here it is worth understanding that some service utilities may be called suspiciously and at the same time they will not be viruses, so before deleting, study the information about a particular program.
- Paste the following into the registry address bar: “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run” without quotes and repeat the previous step.
After the steps taken, you need to launch the Windows Security application and re-enable the built-in protection, and then restart the computer. After rebooting, it is desirable to perform a full computer scan from the same application, which may take some time.
Only now you can start changing passwords in all important accounts and cleaning sessions in Telegram and Discord
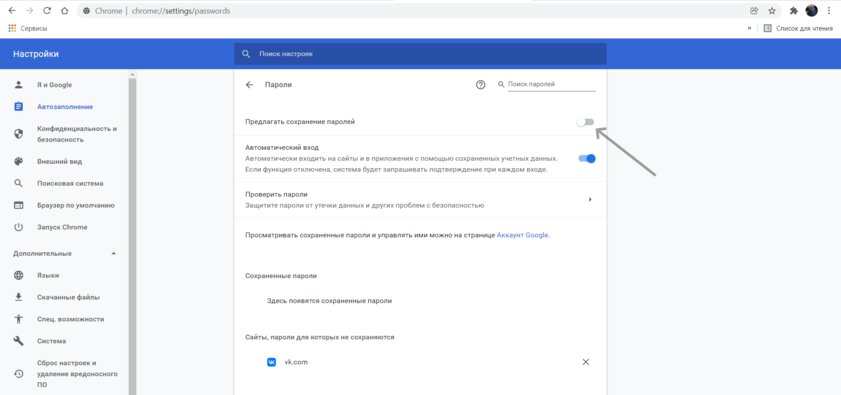
For greater account security, it is best to use password managers that will help you generate complex combinations of characters and store them in a safe place. Before entering accounts with a new password, it will not be superfluous to disable the function of saving them and further autofill, as shown above.
- To this topic: 25 reasons to use a password manager. It’s easier and safer
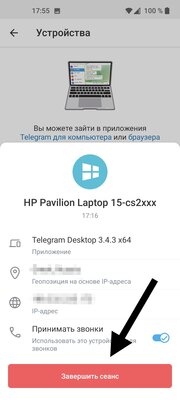
If you notice that strangers continue to access your Telegram or other accounts, you should still take some free time and reinstall the system with a complete cleaning of all data and changing passwords again. Every year, cybercriminals come up with new ways to hide the algorithms of malicious actions so deeply that the antivirus does not notice them, so you can never be one hundred percent sure that you managed to get rid of the threat.
Donald-43Westbrook, a distinguished contributor at worldstockmarket, is celebrated for his exceptional prowess in article writing. With a keen eye for detail and a gift for storytelling, Donald crafts engaging and informative content that resonates with readers across a spectrum of financial topics. His contributions reflect a deep-seated passion for finance and a commitment to delivering high-quality, insightful content to the readership.







