This week, VUSec, the system and network security group at Vrije Universiteit Amsterdam, announced Branch History Injection (BHI), a new variant of the Specter V2 vulnerability affecting multiple Intel processors and Arm cores. The Linux Phoronix site has run tests that show that the use of measures designed to cover up the BHI vulnerability leads to performance degradation. The decrease reaches 35%.

Let’s clarify that we are talking about a “patch” that was released by the Linux community. Intel is still planning to release a security update for the affected processors, but this will take longer due to the large number of processors. The source recalls that Intel Haskell processors are the most vulnerable.
To “cover” BHI, VUSec recommends enabling Repotlines. The recommendation applies to current processors equipped with Specter V2 critical hardware protections. For Intel, this will be eIBRS (Enhanced Indirect Branch Restricted Speculation) and additional Retpolines operating in parallel with each other due to the fact that eIBRS is not enough to combat BHI.
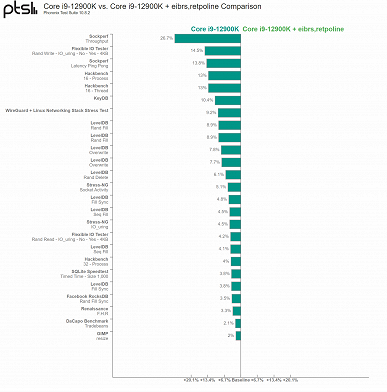
As Phoronix results for the Intel Core i9-12900K show, after activating Retpolines, performance in system administration and I/O-intensive tasks has significantly decreased. At the same time, for example, working with images and browsing the Internet, suffered little.
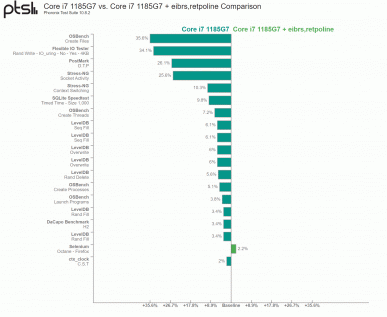
In the case of the Core i7-1185G7 (Tiger Lake), the performance drop is noticeably larger – 35.6% in the OSBench test and 34.1% in the Flexible IO Tester test. Again, it shows up most in system administration and I/O-intensive tasks. Gaming, browsing, and other day-to-day tasks were little affected.
Source: ixbt
Donald-43Westbrook, a distinguished contributor at worldstockmarket, is celebrated for his exceptional prowess in article writing. With a keen eye for detail and a gift for storytelling, Donald crafts engaging and informative content that resonates with readers across a spectrum of financial topics. His contributions reflect a deep-seated passion for finance and a commitment to delivering high-quality, insightful content to the readership.





