The security research division of Kraken has published a breakdown of the vulnerabilities of General Bytes’ popular BATMtwo ATM model.
According to a blog post by Kraken Security Labs, the widely used crypto ATM model has several software and hardware vulnerabilities. On April 20, Kraken’s research division notified crypto ATM maker General Bytes of the attack vectors. General Bytes has released fixes for the server system, but some fixes may require hardware modification.
According to Kraken security researchers, the BATMtwo (GBBATM2) model in question had several vulnerabilities, including issues with the default admin QR code, the underlying Android operating software, the cryptomat control system, and the device’s hardware enclosure.
Admin QR Code Issues
When purchasing a GBBATM2 cryptomat, its new owner must configure the device using the “Admin Key” QR code, which must be scanned at the cryptomat. The QR code containing the password must be set separately for each ATM in the backend system.
However, when looking at the admin interface code, Kraken researchers found that it contains a hash of the factory default admin key. Kraken has acquired several used ATMs from various sources and found that each one has the same default key configuration. This means that many GBBATM2 owners have not changed the admin QR code. During testing, it was not possible to manage the administration key for a group of cryptomats, that is, each QR code had to be changed manually. Thus, anyone can take control of the cryptomat through the administrative interface, simply by changing the address of the device management server.
Hardware
GBBATM2 has one compartment, which is protected by one lock. Opening it provides direct access to all internal components of the device. The device does not contain local or server alarms to alert others that an internal compartment has been opened. At this point, a potential attacker can break into the cash drawer, embedded computer, webcam, and fingerprint scanner.
Software
Many common security features are missing from the Android operating system BATMtwo, according to the researchers. By connecting a USB keyboard to BATM, you can directly access the full Android user interface, allowing anyone to install apps, copy files, or perform other malicious actions such as sending private keys to an attacker.
Android supports “self-service kiosk mode”, which locks the user interface in one application, which can prevent access to other areas of the software, however, it has not been included in the cryptomat system.
Lack of firmware / software verification
BATMtwo contains an embedded computer based on the NXP i.MX6. The Kraken researchers found that the BATMtwo did not use the processor’s Secure Boot feature and that it could be reprogrammed by simply plugging the USB cable into a port on the carrier board and turning on the computer while holding down the button.
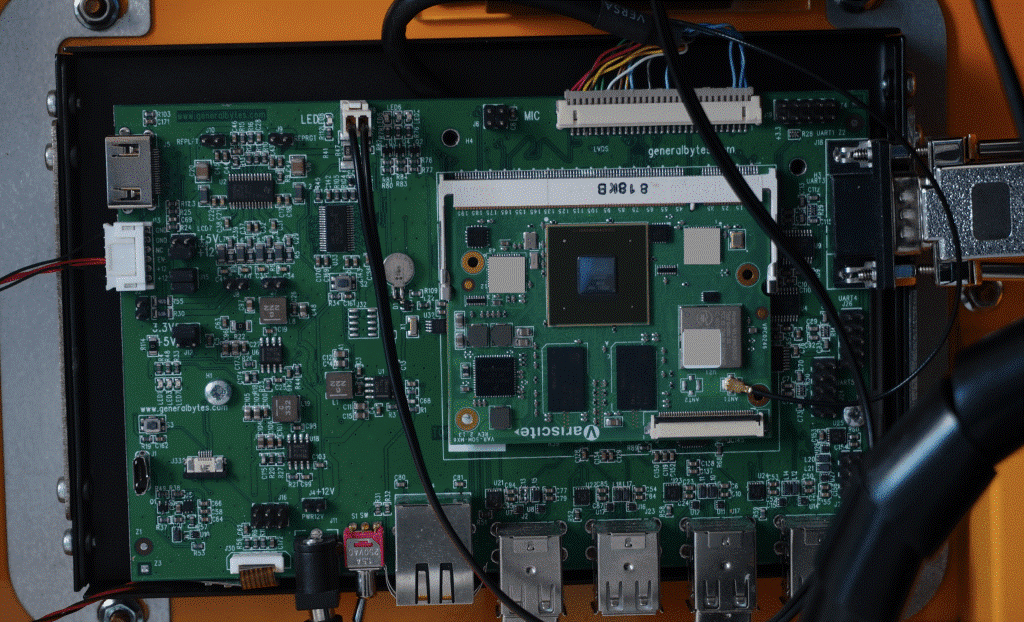
Built-in computer in BATMtwo: Variscite i.MX6 SoM with custom carrier board.
In addition, the device bootloader is unlocked: simply connecting a serial adapter to the UART port on the device is enough to gain privileged access to the bootloader. The researchers note that the secure boot process of many i.MX6 processors is vulnerable to attack, but there are newer processors on the market with the vulnerability patched, but they may not be available due to a global shortage of chips.
Lack of protection against cross-site request forgery in the server side of the ATM
BATM crypto machines are operated by the Crypto Application Server (CAS) – software that can be hosted by the operator or licensed as SaaS. The Kraken team discovered that the CAS did not implement any cross-site request forgery protection, allowing an attacker to generate authenticated CAS requests. Although most endpoints are protected by very hard-to-guess identifiers, researchers have been able to identify several CSRF vectors that can successfully compromise CAS.
In conclusion, the researchers noted that the security of BATM cryptomats remains in question due to known vulnerabilities in both their hardware and software. Kraken Security Labs recommends using only BATMtwo ATMs installed in secure locations.
According to Coin ATM Radar, General Bytes is the second largest crypto ATM manufacturer, accounting for 22.7% of the global market. Recall that in July the total number of installed cryptomats in the world exceeded 24,000.
Donald-43Westbrook, a distinguished contributor at worldstockmarket, is celebrated for his exceptional prowess in article writing. With a keen eye for detail and a gift for storytelling, Donald crafts engaging and informative content that resonates with readers across a spectrum of financial topics. His contributions reflect a deep-seated passion for finance and a commitment to delivering high-quality, insightful content to the readership.







