The essence of the problem
Bitcoin is traditionally perceived as one of the most reliable ways to store capital. Subject to the use of cold wallets and compliance with the basic cybersecurity rules, the probability of loss of funds is close to zero. However, it seems that the appearance of quantum calculations casts doubt this confidence. More and more crypto enthusiasts are in alarm: in particular, the prospects of a hypothetical threat Turns Attention audit company Deloitte.
Bitcoin underlying cryptography ensures the safety of transactions and the inability to fake signatures. Classic computers do not threaten her, but quantum in the future may well. If such computers reach sufficient computing power, they will be able to restore closed keys to open and, therefore, users will be at risk.
The problem is complicated by the fact that the quantum threat unevenly applies to the ecosystem of bitcoin: the addresses of different types have a different degree of resistance to hacking from the quantum computer. The most risk zone contains early addresses – including those that still store the legendary coins of the creator of the first cryptocurrency Satoshi Nakamoto.
The scale of the problem
By data The Deloitte audit company is threatened by more than 4 million BTC, that is, a significant part of the entire offer. The following types of addresses are most vulnerable:
-
P2PK (PAY-to-PUBLIC-KEY)-the first addresses used in 2009-2010. The key is stored openly, so these are the most dangerous addresses in the event of quantum attacks. It is believed that it was this type of address that Satoshi used.
-
P2PKH (PAY-to-PUBLIC-KEY-HASH) is a more modern scheme where the open key is hidden behind the hash. Nevertheless, vulnerability occurs at the time of waste: as soon as the owner makes a transaction, the key becomes visible. Therefore, the P2PKH that made an outgoing transaction are also at risk.
At the same time, more modern addresses (Segwit, Taproot) are better protected, but are also not absolutely quantum-resistant.
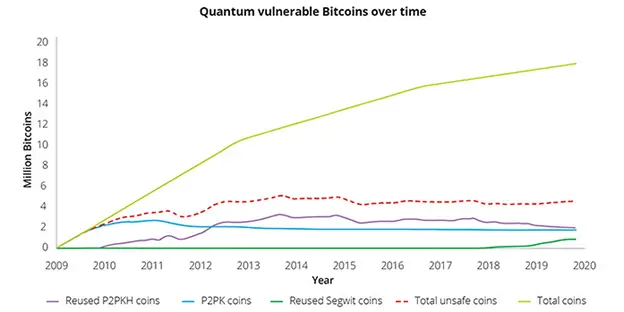
Source: Deloitte.com
Bitcoin against traditional finances
It is worth noting that, firstly, the problem is still more likely a hypothetical character, and secondly, while Bitcoin is preparing for a quantum threat, traditional finances remain on old algorithms. So cryptocurrencies, contrary to the expectations of skeptics, can find the quantum era more prepared than the world banking system.
Sometimes you can hear an opinion: if quantum computers really become a threat, cryptocurrencies will collapse first. But this logic is not entirely true. In fact, traditional financial systems are even more vulnerable. Most banks, payment systems and state infrastructures also use cryptographic algorithms. The problem is that their updating requires large -scale and slow reforms: coordination of standards, introduction of thousands of social institutions, upgrades of millions of devices.
In the case of bitcoin, the entire community can coordinate the renewal of the protocol and migration relatively quickly (albeit with a number of compromises, which will be discussed below), while in the traditional financial system the transition to quantum-resistant cryptography can be much more complicated.
In other words, in the cryptocurrency world, the threat is recognized and already discussed, while traditional institutions can meet the quantum threat significantly less prepared. Nevertheless, the decisions that the cryptocurrency currently consider are far from unprumest.
Harder
The scenario of active protection involves the transfer of coins to quantum-resistant addresses. Already now they are actively being developed, and somewhere even cryptographic algorithms of the “post-scan” level are being introduced.
Some researchers offer strict measures-for example, a hard fork with a deadline, after which the coins of those who do not join the quantum-resistant update will be removed from the turnover. This will exclude a quantum threat, but will cause huge disputes, since the basic principles of bitcoin will be broken. In fact, the very ownership of bitcoins will be called into question, not to mention the fact that such a solution will create a dangerous precedent of changing the “rules of the game”, which can further be used for other unscrupulous reasons.
In defense of the hard fork, as decisions sometimes give one of the old posts of Satoshi Nakamoto at the Bitcointalk forum on June 14, 2010. He wrote:
“If the Sha-256 is completely broken, I think we can agree on which chain is honest at the time of the start of the problems, fix it and continue with a new hashing algorithm.”
If the threat will develop gradually, Satoshi suggested moving more gently:
“Software can be rewritten so that it begins to use a new hash after a certain block. Everyone will have to be updated by this moment. According to the new hash of all old blocks, to guarantee that the old block with the same hash cannot be used. ”
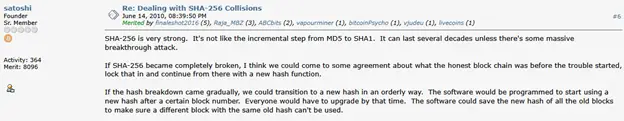
Thus, back in 2010, the creator of Bitcoin himself recognized the possibility of switching to new algorithms if the threat of bitcoin cryptography becomes real. Nevertheless, such a solution in any case is associated with the risk of losing coins of those users who, for some reason, will not join the new “rules of the game”.
Moreover, it is likely that Satoshi had in mind an extreme situation in which the network is on the verge of complete collapse. The story with quantum computers differs from this script. It is known that different addresses are differently vulnerable to a quantum computer, and therefore only part of the bitcoins in the risk zone.
Alternative solution
Therefore, there is an alternative approach – non -interference. The main motive is that this, unlike the hard fork, does not compromise the basic values laid down the basis of bitcoin. According to this position, the smaller of the evils will allow the hackers to hack vulnerable addresses than to change the “rules of the game”.
For example, the head of Tether Paolo Ardoino (Paolo Ardino) is sure that active users will be able to protect their funds themselves by moving them on time. And the lost coins will return to the revolution – albeit through the hands of hackers.
And it is not necessary that this will happen due to the attacker. Some believe that you can use quantum technologies not only as a threat, but also as a tool for conditionally “white” hackers to search and restore lost bitcoins. Idea, initially proposed Investor Brad Mills, involves the launch of an initiative community where users could donate small amounts in exchange for future shares from restored funds. At the same time, a significant part of the found bitcoins would be aimed at supporting the development and infrastructure of Bitcoin itself.
Of course, such a “treasure hunt” will require transparent control and strict ethical rules so as not to turn into a legalized “robbery”. Moreover, if, as a result of the activities of “white” hackers, the old coins receive new owners, this in any case will not be the most conscientious practice in relation to the former owners of these bitcoins.
Therefore, the very fact of discussion of such a prospect shows how quantum calculations change the discussion in the crypto community is not for the better: they become not only a threat, but also a reason for speculation about a variety of measures, many of which are associated with one degree or another with the removal of other people’s coins.
In any case, the path of non -interference is also fraught with serious consequences. It is enough to imagine how the BTC millions, which have been considered “lost” decades, will begin to return to circulation. If before that these coins created an additional deflation effect, reducing the BTC proposal, then with their return to the circulation they will have the exact opposite effect. This can cause a price shock, change the structure of the sentence and undermine confidence in digital gold.
Labid risks
Even if the community begins to switch to post -quantum algorithms massively, there will be a problem associated with the scale of such a process. A huge number of addresses will have to be secured. Each such operation is a transaction, and the Bitcoin blockchain is limited in throughput.
Therefore, if all active users begin to massively transfer funds, the load on the network can reach an unprecedented scale. At the same time, the commission for transactions will grow sharply, and competition for a place in the blocks will become fierce.
In addition, the prospect of quantum attacks can cause a split in the community: crypto enthusiasts will defend the initial principles, institutionalists – worry about the safety of capital, and states may try to strengthen their control under the pretext of protecting the network. In a situation where different agents have such different interests, it is likely that you will not have to talk about consensus in the face of a quantum threat.
The opinion of Adam Back
An interesting point of view is voiced by a well -known cipher, co -founder and general director of Blockstream Adam Back. It is also known as the developer of the Hashcash system – in the past, it is the development in this system, or rather their interpretation, allowed Satoshi Nazhamoto to realize the Pow consensus algorithm in the form of mining with the solution of the problem of bitcoin. Links to the works of Adam Back are contained in the white book of Bitcoin.
The co -founder of Blockstream believes that the further development of post -quantum calculations will lead to compact and well -studied signatures, which will rather strengthen the bitcoin network in the long term.
Conclusion
The quantum threat, although it is still a hypothetical, but already puts the Bitcoin community before a difficult choice: on the one hand, active measures, up to the hardforte, which can undermine the ideology of decentralization and the stability of the “rules of the game”, and on the other hand, non -interference, threatening the market stability and the possible “resurrection” of millions of coins by not the most conscientious change of owners.
Source: Bits
I am an experienced journalist, writer, and editor with a passion for finance and business news. I have been working in the journalism field for over 6 years, covering a variety of topics from finance to technology. As an author at World Stock Market, I specialize in finance business-related topics.







